Introduction: For this assignment I have been asked to create a document that IT managers could use to explain the different threats the school could face. This includes, potential threats to the system, issues regarding malicious damage, counterfeit resources and the organisational impact of any of the threats.
Potential Threats: There are many potential threats that can happen, examples are: Malicious damage, threats related to e-commerce, counterfeit goods and technical failures.
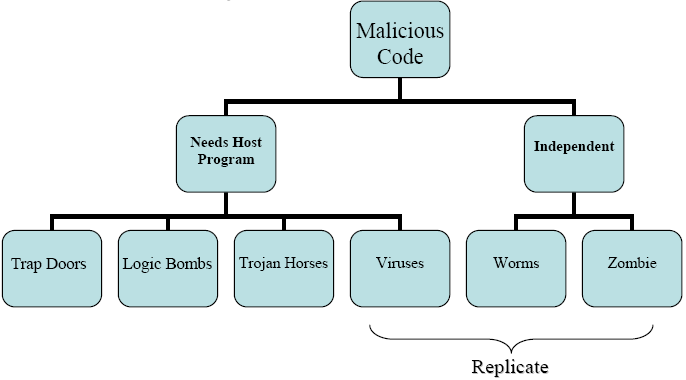
Malicious damage – internal and external damage: Malicious damage is unpredictable and therefore can’t really be prepared for but means that the employer will have to be careful and think about who he is employing. Malicious damage could be done on the spot, with the person having direct access to the system, or it could be done remotely through a virus or worm.
Examples of Malicious damage:
- Smashing windows of the property on purpose.
- Graffiti on the property walls.
- Doors pulled off of their hinges.
- Furniture set on fire.
- Creating large holes in the walls and/or ceilings.
- Theft of landlord property could even be considered malicious damage.
Threats related to E-commerce: website defacement; control of access to data via third party suppliers; other e.g. denial of service attacks.
Counterfeit goods: Counterfeit goods could affect a lot of businesses all around the world and could even affect people individually. For example when people get counterfeit brands which are big like Gucci, Luis Vuitton, Rolex etc they could sell it for very cheap and could cause the real stores with real products to loose money by not selling it . People could get away with all these stuff and when they do the businesses start to worry a lot
Examples of counterfeit goods: Handbags, clothing, accessories perfumes, and electronics and counterfeit money. Illegal websites like 123 movies could put other businesses in a part where it can go bankrupt. legal business like Netflix could loose a lot of money including stores selling film in dds will not be able to sell it because people would just go on websites like 123 movies watching films for free.

Organisational impact: This could be a loss of income , a loss of service , this could give a poor image to the customers.
Examples of Organisational impact: Bad customer service could allow money flowing into the business. This then makes the reputation of the business poor
Loss of service: Loss of service could occur if someone hacks into your Wi-Fi by getting your IP address and then simply ‘booting you offline’, this term ‘booting’ means disconnecting your internet from your router so you cannot access that internet for a certain amount of minutes, hours, days, months, years or maybe for ever having to make you get a new router.
Loss of Business: Loss of business is an organisation who has lost a lot of income due to poor servers and that customers cannot access the website to the business decreasing the amount of customers coming back to the business and the money coming in.

Information security: Information security is a set of security where it protects important/vital information from hackers or people who is trying to make money off it or trying to damage the persons information.
Examples of Information security: Examples are stuff like have a 2 step verification access into your information this will prevent hackers coming into your account.

Advantages and Disadvantages for Information security:
Advantage: It protects all forms of information including digital paper-based, intellectual property, company secrets, data on devices and in the Cloud, hard copies and personal information.
Another advantage of information security is that it keep very important information away from people trying to hack into or steal it and make money off you or harm the persons information.
Disadvantages: Unemployment and lack of job security – This will affect the business in way that they can lose a lot of profit because of the hackers breaching into the software from the business. These hackers could affect so many business all around the world. It could make them go bankrupt.
Another Disadvantage is that if a user misses one single area that should be protected the whole system could be compromised. It can be extremely complicated and users might not totally understand what they are dealing with. It can slow down productivity if a user is constantly having to enter passwords. This is why it can also be a disadvantage
Data integrity: Data integrity is data that is recorded by the company where it is 100% accurate and reliable. So this means if any data is interrupted or messed with the data will remain the same at the end.
Data Completeness: Data completeness is very important because if anything goes wrong with accuracy, the data could give us wrong information and then the data will not be reliable for anyone to use and rely on it.